Windows container install guide
Table of contents
- Deployment architecture
- Prerequisites
- Install object storage app
- Deploy Buzzy app
- Manage ingress traffic
Deployment architecture
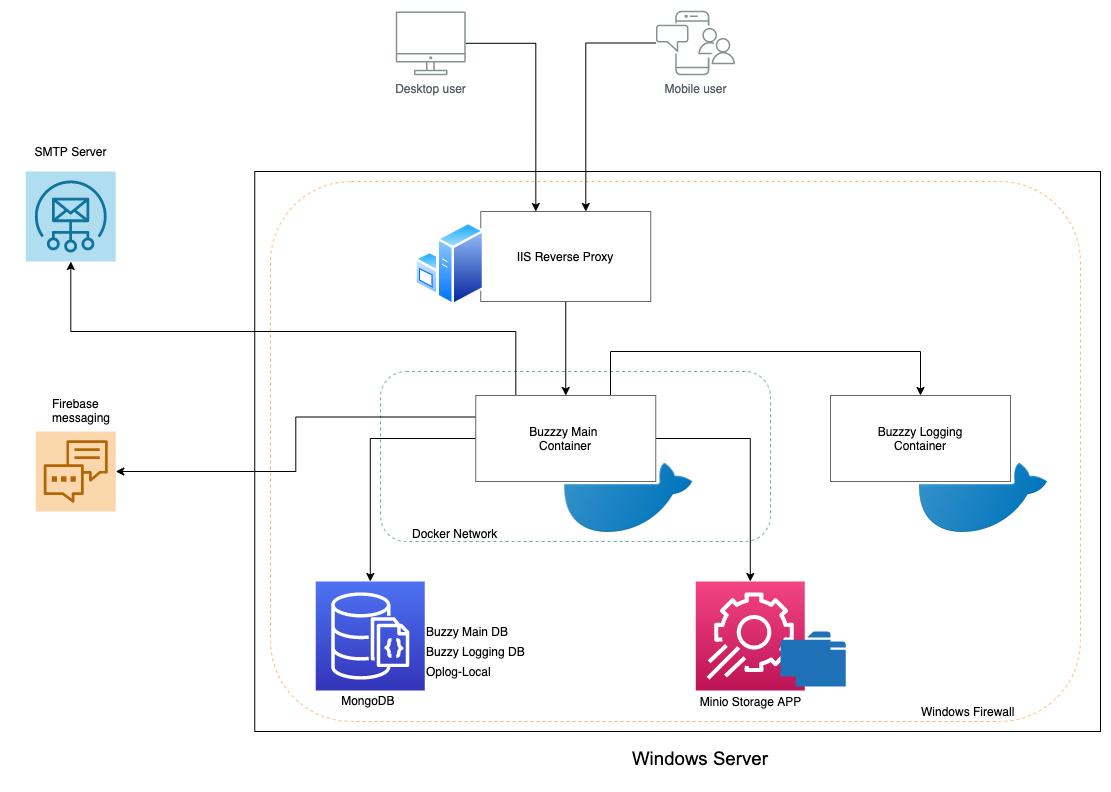
Prerequisites
- Windows Server 2019 with Docker installed
- Two MonogDB databases and oplog (mongoDB cluster in-built local database). MongoDB can be deployed in mongoDB.com, compose.io or as an on-prem installation.
- Allow service ports for MongoDB, Minio and Buzzy from Windows firewall.
Install object storage app
As Buzzy main app requires two S3 compatible object storages, Minio is installed as an S3 compatible object storage application on Windows server.
Download and run Minio:
- Download Minio.exe
- Run Windows batch script below to start Minio service
rem This script starts the Minio app
@echo off
setlocal
path=c:\minio;%path%
set MINIO_ACCESS_KEY=<Minio Access Key>
set MINIO_SECRET_KEY=<Minio Secret Key>
call minio server --config-dir=c:\minio\config --address=:9001 >c:\minio\config.out c:\minio\export
Endlocal
Test Minio service using the browser
Deploy Buzzy app
Buzzy containers are deployed using docker-compose and require YML files including Buzzy configurations for Buzzy main and Logging apps. For this deployment, we use local IP addresses with port numbers to establish connections between services internally. Running a proxy server will be ideal to expose Buzzy service externally. Follwoing steps deploy the Windows image.
- Pull Buzzy Windows image from Buzzy’s Docker registry into your Windows server.
- Create “docker-compose.yml” file using the template provided below and modify configuration values reflecting your environment settings.
YML file:
version: "3"
services:
buzzy:
container_name: buzzy_main
image: buzzybuzz/buzzy-main-windows:latest
ports:
- "9000:3000"
network_mode: "nat"
environment:
ROOT_URL: http://Buzzy Server URL
MONGO_URL: mongodb://<username>:<password>@local IP address:27017/buzzymain
MAIL_URL: “smtp://someuser:somepassword@smtp.sendgrid.net:587”
METEOR_SETTINGS: '{
"jwtSecret": "change-to-some-very-long-secret-string",
"REPORT_ABUSE_EMAILS": ["someadminemail@emails.email"],
"AWS_BUZZY_FILES": {
"enabled": true,
"accessKeyId": "Minio access key id",
"secretAccessKey": "Minio access key",
"endpoint": "http://Minio server IP address:port",
"BUCKET_NAME": "buzzy-files",
"PUBLIC_BUCKET_NAME": "buzzy-files-public",
"S3_REGION": "",
"s3ForcePathStyle": true,
"signatureVersion": "v4"
},
"MAIL_URL": ""smtp://someuser:somepassword@smtp.sendgrid.net:587 ",
"BUZZY_ADMIN_EMAIL": "someadminemail",
"BUZZY_ADMIN_IDS": ["adminuserid"],
"BUZZY_LOGGING_TOKEN": "somelongtoken",
"BUZZY_ADMIN_TOKEN": "somelongtoken",
"BUZZY_CREATE_DEFAULT_ACCOUNTS": {
"enabled": true,
"accounts": [
{
"email": "someone@test.com",
"password": "somepassword",
"isAdmin": true
}
]
},
"public": {
"BUZZY_DONOTREPLY_EMAIL": "donotreply2@buzzy.buzz",
"AWS_BUZZY_FILES": {
"enabled": true,
"S3FileExpiry": 604800,
"BUCKET_NAME": "buzzy-files",
"PUBLIC_BUCKET_NAME": "buzzy-files-public",
"s3ForcePathStyle": true,
"URL_PATTERN": "http:// Minio Server IP address:port"
},
"LOGINS": {
"SELF_REGISTRATION": {
"enabled": true
}
},
"BUZZY_CUSTOM": {
"NAME": "Orgnisation Name",
"APP_URL_IOS": "",
"APP_URL_ANDROID": "",
"LOGO_MAIN": "",
"LOGO_MAIL": "",
"LOGO_MAIL_WIDTH": "60",
"LOGO_MAIL_HEIGHT": "25",
"EMAIL_FOOTER": "",
"PROMO": "",
"PROMO_URL": "",
"SPLASH_IMAGE": "",
"WELCOME_IMAGE": ""
},
"BUZZY_LOGGING_SERVER": "https://Logging server URL",
"BUZZY_TEMPLATE_SERVER": "https://a.buzzy.buzz",
"BUZZY_VERSION": "3.0.1"
}
}'
So far, you have completed following components using above steps.
- Buzzy image pulled from Buzzy Docker repository
- Minio application installed and running
- docker-compose.yml file is created
Now, run docker-compose up command in Powershell or command prompt to deploy Buzzy main app.
PS C:\buzzy> docker-compose up
Check the connection to the Buzzy app (locally) using the browser URL http://localhost:9000
After deploying an ingress service as the below section, you may have to change the ROOT_URL value in the YML file to reflect your externally accessible DNS name.
Manage ingress traffic
Buzzy application running in Windows docker container can be exposed externally depending on the deployment environment. Following are possible options:
A load balancer, application gateway or reverse proxy service. Refer Azure application gateway or AWS application loadbalancer (ALB) documentations. AWS ALB documentation Azure application gateway documentation
Use IIS with URL Rewrite as a reverse proxy. You may install and configure IIS in the same Windows server that runs Buzzy container to route external ingress traffic using URL Rewrite rules. Refer to IIS documentation..